
 |
| Image via CrunchBase |
 |
| Spicy Stories (July 1929) -- Don't Show Everything !! ... Americans still lax with Wi-Fi security: survey -- "Anyone can see everything you are doing," Whitman finished her sentence. (November 7, 2011) ... (Photo credit: marsmet463) |
technology expert, Bill Winterberg. Using a smartphone’s cellular network ... is more secure, he advised, saying that using a cellular network is going to make it more difficult for hackers to “snoop.”
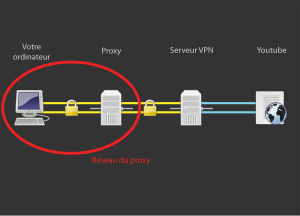 |
| English: How doses work a VPN ? Français : Comment fonctionne un VPN ? (Photo credit: Wikipedia) |
Many companies offer employee access to an internal VPN, but advisors can also check out independent services including TorVPN and Private Internet Access. ...
3. Stay Logged On At Your Peril—... [Not] logging out means that cyber crooks intent on accessing your unprotected Internet sessions could stay on longer, increasing the potential danger, Winterberg says. ...
4. Keep Up-To-Date—Advisors should be updating their software and apps as often as possible, especially when those updates that include security improvements. ...
5. Forewarned Is Forearmed—A security system is only as good as its weakest link, says John Sileo, founder of Silio.com and a speaker on privacy and data security. Advisors should train staff to use best data security practices and recognize potential threats such as spear phishing attacks—emails that may deliver malware software to your computer or mobile devices.
“The number one way we see data stolen is that someone inside his organization is socially engineered out of the data,” Sileo says. Plus, staff training is comparatively cheaper than the estimated $300 per record lost in an average data breach.
6. Triple Check—Even with staff training, advisors should have redundancies in place to keep cyber thieves from impersonating clients, says Adam Levin, former director of the New Jersey Division of Consumer Affairs and co-founder of Credit.com and Identity Theft 911. Although many clients use email—which Leven calls an “inherently unsecure conduit”—to regularly communicate [with] their advisor, there should be a system in place to verify the identity of a client, including follow-up phone calls or in-person meetings. ...
 |
| Harris Interactive (Photo credit: Wikipedia) |
8. Solid Defenses—Not only should advisors use passwords, they also need to use passwords that are long—generally at least six to nine characters—without having personal details such as birthday, age or social security numbers worked in.
Go beyond the typical 4-digit automatic password option available on smartphones, says Winterberg. While it’s inconvenient to have a long password, the 4-digit approach does not provide enough defense against a “brute force” attack.
9. Think Disposable—At the end of the day, smartphones and to some extent, tablet devices, should be treated as throwaway devices. All information stored on the device needs to be backed up in case something should happen, including loss and theft.
“The most important thing is that people need to look at their mobile device and realize that it is not a communication device, it’s a data storage device,” Levin says.
10. Wipe It Clean—While the Find My iPhone app is designed for iPhone users, there are also similar Android versions on the market. Every data security interviewed for this article recommended that advisors have a version on their mobile devices.
Not only can the app help find the phone or tablet if it’s activated, but the app has a “destroy after reading”-like capability that erase all data on the device in case of emergency.
“You can never be too safe,” Levin said, adding that cyber attacks are only going to become more sophisticated and more damaging as technology improves.
'via Blog this'











No comments:
Post a Comment